Ian
Administrator
- Joined
- Feb 23, 2002
- Messages
- 19,883
- Reaction score
- 1,514
A new type of exploit has been discovered which can spread to many different devices via Bluetooth, without connecting or having any interaction from the user. This exploit could spread very quickly now that details have been made public, as it would only take a few seed devices for a virus to spread en-mass.
Ars Technica have a detailed article which includes some example videos of the exploit in action:
https://arstechnica.com/information...s-of-devices-to-attacks-no-clicking-required/
Microsoft and Apple devices have already been patched, as long as you're using the latest versions (and up to date with security patches). However, Android and Linux devices are particularly vulnerably - especially if you're using a non-Google Android phone (i.e. Samsung S7/S8).
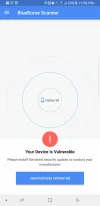
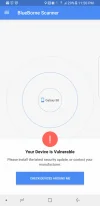
You could download the Blueborne scanner for your Android phone and it'll tell you if you're vulnerable - plus it will scan for other BT devices in range that are also susceptible:
https://play.google.com/store/apps/details?id=com.armis.blueborne_detector&hl=en_GB
Ars Technica have a detailed article which includes some example videos of the exploit in action:
https://arstechnica.com/information...s-of-devices-to-attacks-no-clicking-required/
Microsoft and Apple devices have already been patched, as long as you're using the latest versions (and up to date with security patches). However, Android and Linux devices are particularly vulnerably - especially if you're using a non-Google Android phone (i.e. Samsung S7/S8).
You could download the Blueborne scanner for your Android phone and it'll tell you if you're vulnerable - plus it will scan for other BT devices in range that are also susceptible:
https://play.google.com/store/apps/details?id=com.armis.blueborne_detector&hl=en_GB



 )... But I haven't had the chance to properly investigate this until today, as I have been very busy during the past month.
)... But I haven't had the chance to properly investigate this until today, as I have been very busy during the past month.